With a growing number of sites facing increasing attacks, users are beginning to understand the importance of choosing secure websites.
Google even stated this to be a ranking factor in 2017, so it's a preferred factor we encourage all our clients to implement on their website.
HTTPS is slowly moving away from being an option to something that will become the de facto filter of users when choosing a service or product.
So, how can you ensure your site is secure with HTTPS?
In this blog, we’ll walk you through how to implement HTTPS the right way, followed by the most common HTTPS mistakes that can sabotage your efforts.
How To Set Up HTTPS The Right Way
Obtain and Install an SSL Certificate
You might be wondering, “What is an SSL certificate?”
An SSL Certificate stands for Secure Sockets Layer Certificate, which is really just a fancy way of saying:
It’s the padlock for your website.
It encrypts all the information your visitors send through your site, like credit card details, passwords, and contact forms, keeping it private and secure from hackers. This encryption scrambles the data during transmission so no one can intercept or read it.
It also tells Google your site is legit, helping protect you from fake or malicious sites that try to impersonate your business (and trust us when we say hackers are very good at mimicking real brands).
How do you get one?
There are a few options, and not every site follows the same process, but we’ll walk you through a frequently used and simple method.
The simplest way to get an SSL Certificate is through your hosting provider (e.g. GoDaddy, SiteGround, Bluehost, HostGator).
Follow these steps:
- Log into your hosting account.
- Find the “SSL,” “Security,” or “SSL/TLS” section in your dashboard.
- Click “Activate” or “Install SSL” (look for options like “Free SSL Available” or “Activate HTTPS”).
- Wait a minute or two, then enable “Force HTTPS” or “Auto Redirect to HTTPS”.
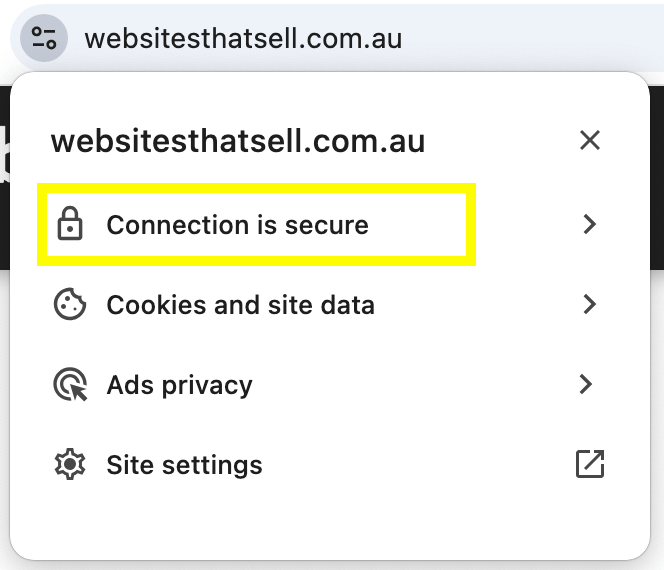
- Visit your website—you should now see the padlock icon in your browser's address bar.
Not bad, right?
But just like a car, even if it starts, it’s smart to check under the hood. The same goes for your website. Here are a few best practices to ensure your host has done their job and everything’s running smoothly:
- Test your site: Visit it manually, or use a free SSL tester tool like SSL Labs to check your setup.
- Update search engines: If you use Google Search Console, re-verify your site under the new HTTPS version.
- Add extra protection: Consider enabling HTTP Strict Transport Security (HSTS) to make sure browsers always load your site securely.
Once these steps are complete, your site should be secure, trusted, and optimised for both users and search engines.
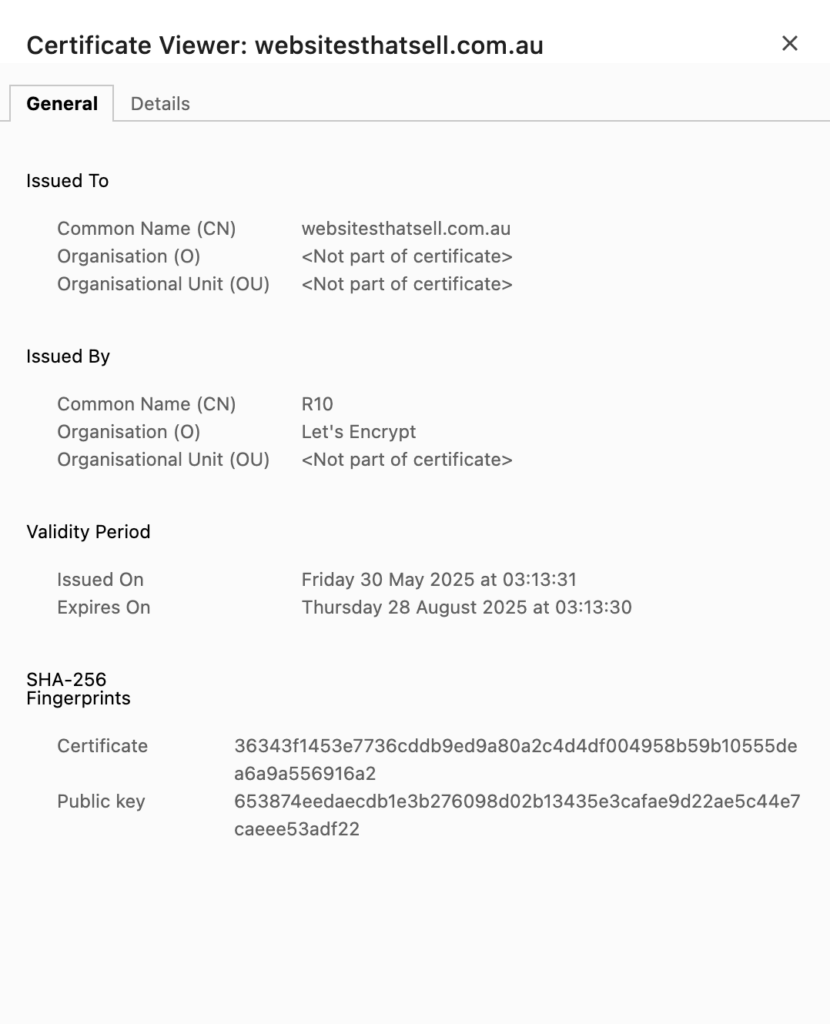
This is what you want to see on your website:
7 Common HTTPS Implementation Mistakes
So, what if something goes wrong?
Maybe the padlock doesn’t show up… or your users are still getting warning messages. Whatever the case, it’s often due to one of these common HTTPS mistakes.
Let’s break them down:
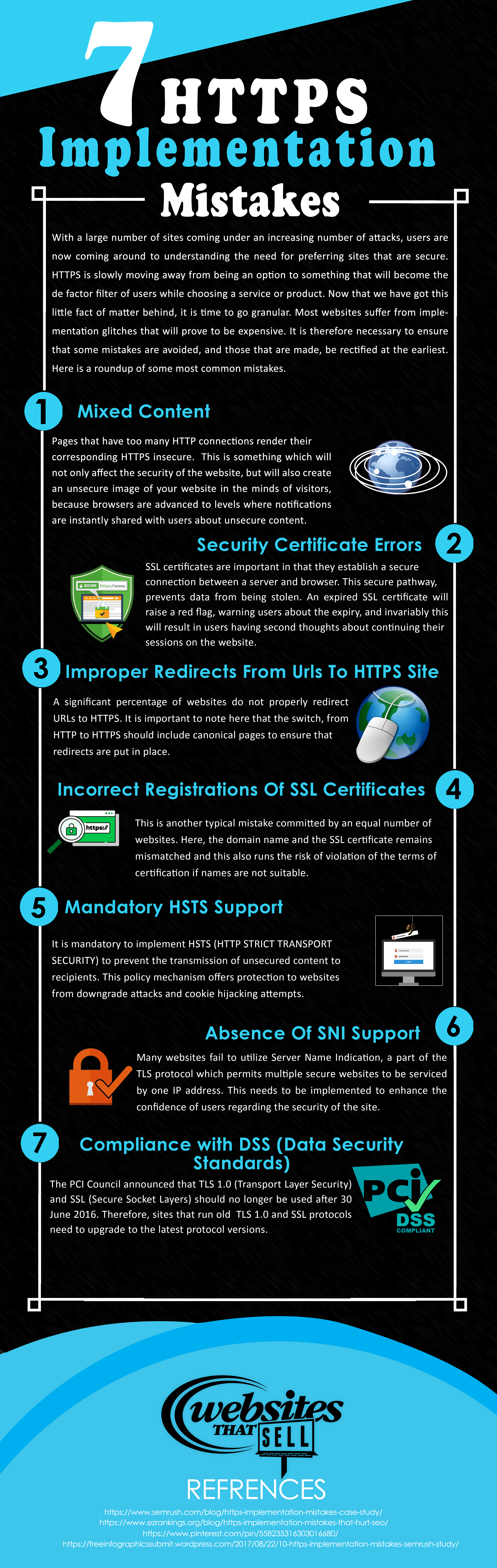
1. Mixed Content:
Mixed content happens when a webpage is loaded over HTTPS but includes even one resource, such as an image, video, script, or stylesheet, loaded over HTTP. This undermines the security of the entire page as it creates a vulnerability that attackers can exploit.
Even a single HTTP connection on an otherwise secure HTTPS page can trigger browser warnings. Modern browsers are designed to instantly notify users of unsecured content, which can damage trust and make your website appear unprofessional or unsafe. To avoid this, make sure all resources on your site use HTTPS, including images, CSS, JavaScript files, and external links.
2. Security Certificate Errors:
SSL certificates are important in that they establish a secure connection between a server and browser. This secure pathway prevents data from being stolen. An expired SSL certificate will raise a red flag, warning users about the expiry, and invariably this will result in users having second thoughts about continuing their sessions on the website.
3. Improper Redirects From URLs To HTTPS Site:
A significant percentage of websites do not properly redirect URLs to HTTPS. It is important to note here that the switch, from HTTP to HTTPS should include canonical pages to ensure that redirects are put in place.
4. Incorrect Registration of SSL Certificates:
This is another typical mistake committed by an equal number of websites. Here, the domain name and the SSL certificate remain mismatched and this also runs the risk of violation of the terms of certification if names are not suitable.
5. Mandatory HSTS Support:
It is mandatory to implement HSTS (HTTP STRICT TRANSPORT SECURITY) to prevent the transmission of unsecured content to recipients. This policy mechanism offers protection to websites from downgrade attacks and cookie hijacking attempts.
6. Absence of SNI Support:
Many websites fail to utilize Server Name Indication, a part of the TLS protocol which permits multiple secure websites to be serviced by one IP address. This needs to be implemented to enhance the confidence of users regarding the security of the site.
7. Compliance With DSS (Data Security Standards):
The PCI Council announced that TLS 1.0 (Transport Layer Security) and SSL (Secure Socket Layers) should no longer be used after 30 June 2016. Therefore, sites that run old TLS 1.0 and SSL protocols need to upgrade to the latest protocol versions.
Conclusion
HTTPS is no longer just a nice-to-have feature for websites; it’s a critical element in today’s digital landscape. As cyber threats continue to rise, securing your site with HTTPS helps protect your users’ data and establishes trust with your audience. Google has made HTTPS a ranking factor, meaning that secure websites are more likely to appear higher in search results. This makes HTTPS important not only for security but also for SEO performance.
However, implementing HTTPS comes with its own set of challenges. Many websites fall prey to common mistakes like mixed content issues, incorrect SSL certificates, or improper redirects, which can jeopardise both security and user trust.
At Websites That Sell, we specialise in ensuring your website is fully secure and optimised for search engines. From proper HTTPS setup to ongoing website development & website maintenance and security monitoring, our website development team handles it all. We have the expertise to keep your website safe and performing at its best. Need help? Call us at 1300 974 367.

